Introduction
Wikibon held a Peer Incite on the subject of Backup is Broken, and concluded that backup had to move from a window model to a service model. Traditional backup technologies require a backup window, which is increasingly an impediment to the data protection SLAs demanded by the business. Array-based replication technologies provide good SLAs but are costly and difficult to manage. The current technologies do not meet the requirements of many parts of the business and are an impediment to establishing IT as a service with Infrastructure 2.0. The requirement is a common application data protection model that can be tuned to the specific line-of-business budgets and departmental SLAs. It particular it has to meet the protection and recovery requirements of a virtualized environment.
Some important technologies have allowed the previous batch model to be replaced by a continuous backup model. These include:
- The ability to take application-consistent copies of data almost instantaneously and highly efficiently. Virtualized storage arrays have been the design point for storage arrays, as the virtualized architecture allows just the pointers to the blocks to be copied. Some applications also provide this snapshot capability.
- Operating system services such as Microsoft VSS that allow the storage volumes to reflect a consistent set of data at a point in time;
- De-duplication and compression functionality within the storage array or application to minimize backup storage space and (optionally) to minimize line costs for remote replication;
- Backup suites which take advantage of the new technologies and provide integrated backup and restore capabilities.
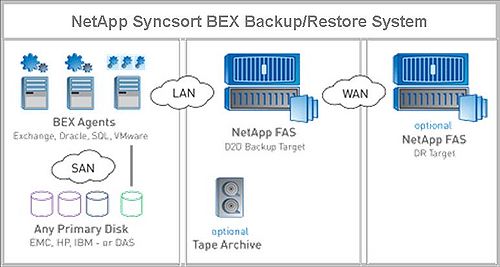
Example: NetApp/Syncsort Solution
The NetApp/Synchsort BEX solution shown in Figure 1 is a good example of this continuous backup model.
Snapshots and replication do not in themselves provide a secure backup system or a robust recovery system. The backup data has to be catalogued, integrated, and managed to provide these services. In Figure 1, the Syncsort BEX system provides these services through agents in the servers. The users that Wikibon has talked to have commented positively on the rich set of restore capabilities, including application and bare-metal recovery, physical-to-virtual and virtual-to-virtual recovery for VMware environments, file/object recovery and the recovery of a backup dataset as a VM. All the functionality is managed from a single console.
Wikibon believes that this is the new model of data protection that is emerging. It is based underlying snapshot technologies, i.e., consistent snapshots will be taken on a regular basis, and the incremental data from the last snapshot moved to a separate site. The level of service can be adjusted by varying how often the snapshots are run, how quickly they are transferred (mainly determined by telecommunication line speed), and how quickly the data can be recovered (quality of recovery system and amount of recovery data held locally and remotely). This allows the service to be tailored to meet the business recover time and budget requirements. Most important of all, it eliminates the backup window. This model offers a far more flexible and cost-effective strategy to meet Infrastructure 2.0 requirements than the traditional one-size-fits-all backup window model.
Constraints to Adoption
Wikibon sees four major constraints to adoption of a service model for backup:
- The availability of applications and operating system that support consistent snapshots. This is currently easiest in a Windows environment with VSS.
- The understandable reluctance to make major changes to complex data protection processes and procedures that work. Movement is likely to take place on an application-by-application basis, as new versions of software are implemented.
- The desire for support for this model from the major backup software providers. Wikibon believes that change is happening but at a glacial place. Solutions such as those from NetApp and Syncsort are filling the vacuum.
- Reluctance for change within the organization: Wikibon observed that organizations that have adopted the new model did so because of severe pain in one area. CIOs need to provide the capability of selective higher and lower functionality for lines-of-business or see them look for Cloud alternatives that either provide better service levels or lower cost alternatives.
Wikibon believes that all these constraints will be reduced in importance as this model takes hold as best practice over the next few years.
Action Item: This approach is ideal for a Windows-only environment, either for a small business or for part of a larger data center. Senior executives should look at this approach for solving backup window problems ahead of pure data de-duplication technology. This will put them on a better strategic path for meeting increasing aggressive service requirements as the business starts to evaluate in-house services against alternative cloud services.
Footnotes: