Elastic computing (the “cloud”) provides a tremendous opportunity for IT to transition to a variable cost structure and set of services sold to and consumed by revenue-generating businesses and applications. While the journey to public or hybrid cloud infrastructure for the most mission-critical applications of an organization may take a while, the technologies and level of integration available today will continue to mature and certainly lead to this fundamental change in the use of information technologies.
Contents |
Amazon EC2 Leading the Pack
A journey leader in this change-over is Amazon. Amazon has spent over a decade and over $2B running some of the world’s most scalable and sophisticated infrastructure and in developing significant expertise in building, operating, and maintaining the worldwide infrastructure. With this cache of infrastructure and expertise, the Amazon Web Services (AWS) is now estimated to be provisioning 50,000 elastic computing (EC2) server instances per day. This estimate comes from Goldman Sachs after examining EC2 resource IDs and doing a time-series analysis on how much the IDs are incremented per hour. This translates into an estimate of 18 million provisioned server instances per year. Confirmed, no? Busted, no? Plausible, maybe? And by way of comparison, total server shipments worldwide for Q209 were around 1.4 million.
On Boarding Users and Workloads
Just one of the challenges to Amazon and EC2 customers with this degree of computing elasticity is getting users onto and off of each instance at the right time, with the right access privileges, and with the capability to follow and report EC2 user activity. These capabilities are important for almost all classes of workloads moving to the cloud and are even more significant to those considering the move of more mission critical (classes 2, 3 and 4) applications.
And EC2 customers typically want as much delivered on demand and from the cloud as possible, but one-off security solutions don't work given the variability of end-user systems and difficulties associated with identity and access management integration. In addition, some tried-and-true identity management standards (e.g., SAML) work well in multi-tenant environments, and new standards (e.g., MSFT ADFS) appear well positioned to improve security and reduce complexity in cloud environments.
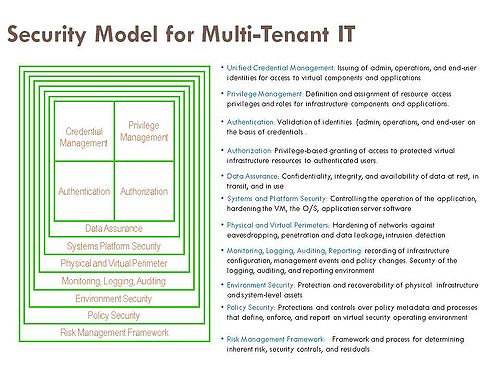
So Amazon announced a partnership with Symplified to provide an identity and trust integration layer that extends enterprise on-premises identity and access infrastructure to Amazon EC2 workloads. They call this the Trust Cloud. The Amazon/Symplified solution provides credential management, provisioning, authentication, authentication, and auditing as a set of security services within a model of what’s needed for security in multi-tenant IT environments, as shown above.
What this Means to End-Users
There are 3 important takeaways for end-users to consider in this step toward a maturity in computing on demand:
- Amazon and Symplified understand that user management, access, and audit side of workload provisioning/deprovisioning must be as elastic as the computing platform in order meet the growing customer demand for EC2 services.
- Credentially, user provisioning, authentication, and authentication, the workloads once deemed too sensitive to be managed outside the data center, are moving to the cloud using tried-and-true and emerging security standards;
- Progress continues on the identity management front. The Trust Cloud is the latest instantiation of an internet identity infrastructure that began with things like digital certificates, Identrust, ABA eCom, and other PKI-based technologies, services, and standards.
Bottom Line
Amazon has commoditized IT further by offering some security capabilities as “dial-tone” to EC2 customers in an effort to capitalize on an IT market shift to the cloud. And Symplified continues to demonstrate Security as a Service leadership, expanding capabilities, attracting partners with strong technology and value propositions, and its capability to deliver standards-based technologies and services for a core infrastructure workload that underpins trust in cloud services.
Action Item: Business managers, end-users, CIOs, and CTOs using or moving application workloads to EC2 should begin to kick the tires of the Trust Cloud and the Amazon/Symplified security service and measure the value vs. cost. In-and-of-themselves, identity and access management as a workload are mission-critical to most if not all organizations. So care should be taken to ensure the desired level of service and security can be achieved.
Footnotes: