Security
Security integration increases the economic value of virtual computing. Most value will come from the ability to encapsulate individual applications (including users, databases, and software) in the VM, and effectively maintaining the confidentiality, integrity, and availability of the application/VM/OS container across processors and locations. The virtualization layer’s encapsulation can provide inherent multitenancy regardless of the physical infrastructure, but requires auditability.
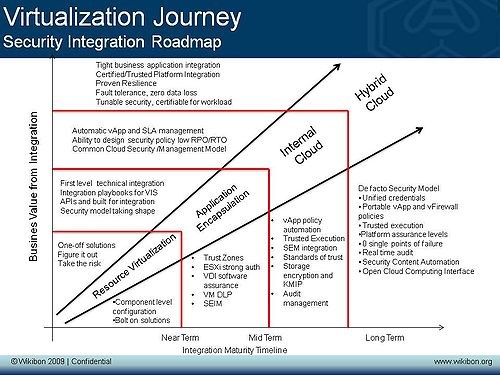
Value of Security Integration
The chart above describes this roadmap of security integration over a timeline and the value generated in soft dollar terms from the depth and scale of the integration.
Security Milestones
The journey to integrating security into the virtualization environment must have:
- Resource Virtualization where the resources of a data center are virtualized, including servers, storage and networking. This allows virtual machines (VMs) to run applications, and be mapped against real resources.
- ability to lock down the hypervisor
- ability to segregate intra VM communications
- basic user authentication and resource authorization
- data in transit and at rest monitoring
- provisioning control
- configuration management
- hardware-level enforcement of the hypervisor to secure next-generation virtualization-specific attack vectors
- compliance and remediation against hypervisory hardening state
- Application Encapsulation or creation of vApps is the next milestone. Virtual applications (vApps) are created together with the data and metadata required to define the resources and service levels required to execute the vApp.
- Trust Zones (e.g., vShield, VMSafe)
- vApp security policy
- Root of trust for workload
- Discretionary access control
- Internal Cloud enables location independence of vApps so that it can be moved between virtual machines, physical machines and internal locations. The data associated with the application can be moved or replicated and the state of the application preserved.
- ability to move workloads and trust zones from machine to machine
- maintenance and monitoring of policy compliance regardless of workload location
- non-discretionary access control
- storage encryption, key management
- vApp policy automation
- security and event management
- problem and change management automation
- simple, point-in-time auditing
- unified user and credential management and access provisioning (IAM).
- Hybrid Cloud enables external location independence of the vApp, so that the application or part of the application can be moved outside the organization into externally available resources.
- multi-tenant encryption, data dispersal, key management
- federated IAM
- mandatory access control
- compliance monitoring per workload
- platform assurance certification
- continuous audit
- multi-tenant end-user self-provisioning/chargeback portal
- multi-tenant security (demonstrable security posture) portal
Action Item:
Footnotes: This research is an expansion of a section of research looking into The Value of the VMware Integration Journey