Cloud-based desktop application services (Google Apps) are a component of Google’s strategy to expand into new businesses that augment its Internet search and advertising prowess. To be successful, the search engine has trained its array of computers and data analysis acumen on these new business imperatives of small and large businesses alike to fuel future growth and its market making capabilities.
- Cost Takeout and Efficiency
- Customer Value and Growth Creations
- Proactive Risk Management and Governance
Efficiency, Value, Risk
Google has made several moves to tie the transition to Google Apps to these business imperatives and entice more companies away from the Microsoft desktop. For example, in 2Q2009, Google made available a uniform way for programmers to incorporate Google's search engine, spreadsheet, maps, videos, and e-mail software into their own applications, giving users a single point of entry into the complete desktop platform. Google also continues to tout a price-point that’s 50% of a typical Microsoft per seat desktop cost. Google Chrome OS also hopes to redefine a laptop into a Net appliance that relies almost entirely on the cloud for the apps people would use routinely. And Google keeps pushing - Google Wave promises to attack one of Microsoft's most beloved products, its SharePoint collaboration software. All these moves translate into a cost takeout, efficiency, and portability value proposition for organizations large and small.
On the topic of value and growth creation, Google has enabled mobile computing that works with customer management enterprise software to pinpoint contacts or tally relevant expenses based on where a sales person is based and lets companies import data from business applications such as SAP (SAP) and Oracle (ORCL) into Google Spreadsheets.
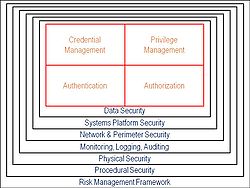
For the requirements of proactive risk management, Google has a number of initiatives underway, including its partnership with Symplified to provide identity and access management that extends existing enterprise investments in security platforms to cloud-based applications, provides a needed measure of control over important identity operations and access management operations and is standards-based, promoting interoperability.
Symplified – Underpinning Trust in Google Desktop Applications
Symplified underpins trust in services by providing an open identity and access management platform. Symplified provides a unified access management system purposely built for the cloud architectures and services delivered via SaaS. Symplified’s standards-based technologies propose to integrate enterprise user directors and access management systems with what’s needed to establish, provision, enroll, and manage identity across virtual computing environments. The value proposition is about streamlined management, reduced costs, an open platform for growth and expansion, and improved security. Part of this value proposition is a Web access infrastructure, a second- or third-generation light-weight product. The Symplified platform is offered as a third-party service or as an enterprise appliance.
The Symplified management team has heritage in the security software industry. Its founding management brings security software entrepreneurs with 50+ years of experience that have consistently held market leadership roles in Web security and mission-critical IT management software.
Identity Partnership - Reducing Identity Stores Makes Perfect Sense
A partnership on identity and access management only makes sense when considering where identity is heading and challenges associated with virtualizing traditional datacenter workloads. Identity and identity management is a cost center for most if not all organizations – it’s not a basis for competition or product differentiation. And until the holy grail of identity management and security for competitive advantage is achieved, if ever, organizations will look to cut identity costs out of the data center and risk manager’s budget.
The partnership between Symplified and largest SaaS application providers like Google, SalesForce, and others does just that. It provides the ability to leverage existing identity investments while at the same time creating a platform to securely transition the identity and access management costs out of the enterprise.
Imagine the costs otherwise – for each new workload moving to the Cloud, organizations would need to establish new identity and access management operations to accomplish things like identity vetting, identity creation, credential management, provisioning and revoking user access rights, and auditing identity events and activities. More silos, more costs, more opportunities for identity and access management errors, and more enterprise risks.
Futures and Concerns
The suggestion of relegating identity management workloads to the Cloud may seem like heresy to risk managers, but CISOs, CEOs, and CIO should understand the opportunity, the costs, and the risks when making sourcing decisions that involve Cloud services. The results of this assessment may be surprising, and of course, “your mileage may vary”.
And the success of the Symplified/Google partnership in providing cloud-based identity services is tied to a few important indicators, all of which are pointed in a favorable direction:
- The trend line for continued transition to SaaS for desktop, sales force automation, human capital management, Web 2.0, collaboration management, content management, ERP, and other applications,
- A strong, demonstrable ROI/TOC for transitioning identity workloads to the cloud, and,
- The ability for Symplified to demonstrate Security as a Service leadership, expand capabilities (e.g., incorporate user-driven identity) and attract XaaS partners with strong technology and value propositions, and
- Its continued capability to deliver safe and reliable technologies and services for an infrastructure workload that underpins trust in cloud services.
Action Item: Identity management is just one of those hidden compliance and due care costs associated with the move to virtual computing. As with many other datacenter workloads that are not directly tied to revenue generation or competitive advantage, there will be increased pressure on the CIO and CISO to find secure and cost-effective alternatives. CIOs and CISO need to understand and be able to effectively communicate these options to the businesses that own risk and own identity.
Footnotes: